Jason Lowery - Softwar, part IV
| Dear Hiveans | Liebe Hiver | Queridos Hiveanos |
|---|---|---|
| This is part 4 (the last part) of my favourite excerpts from the book "Softwar" (goodreads) by Jason Lowery. | Dies ist Teil 4 (der letzte Teil) meiner Lieblingsauszüge aus dem Buch "Softwar" (goodreads) von Jason Lowery. | Esta es la cuarta parte (la última) de mis extractos favoritos del libro "Softwar" (goodreads) de Jason Lowery. |
A core lesson of computer science is that computer programs don’t physically exist. They are abstract concepts hypostatized as concretely real things for the sake of reducing the intellectual effort required to use stored-program general-purpose state mechanisms. Although society has adopted the habit of describing software as if it were a physical thing that is “loaded” onto a computer, it simply isn’t. And although society has adopted the habit of describing software as if it were comprised of an orientation of objects (e.g. folder, trash can, recycle bin, thumb nail), it simply isn’t. This is merely an abstraction technique used to make it easier to understand the complex emergent behavior of computer programs. Modern computers are usually made of complex circuitry and electrons stored in floating gate transistors. When a program is “stored” onto a computer, nothing is physically added to the machine. The computer remains the same general-purpose state machine built out of the same complex circuitry and electrons stored in floating gate transistors. When a program is “removed” from a computer, nothing is physically
removed from the machine. … The only physical change that occurs is a state change in the circuitry of the machine. A switch is flipped, or electrons move from one side of a floating gate transistor to another.
Therein lies the fundamental challenge of software security engineering; it requires an engineer who can understand and anticipate different combinations of control actions or inaction which should or shouldn’t occur. Software security engineers must be able to recognize these sensitive control signals and design control structures which eliminate or constrain those signals, which is quite hard to do using only logical constraints encoded into software, while still meeting desired functionality and behavior. This is one of the biggest challenges in software security which makes it so different from security engineering in other industries. Because software doesn’t physically exist, it’s not possible to secure software using physical
constraints unless the underlying state mechanism is physically constrained (this is the single most important concept that the reader should note prior to a discussion about proof-of-work physical cost function protocols like Bitcoin, because what proof-of-work represents is the act of physically constraining software by physically constraining the underlying state mechanism).
But why exactly is it so challenging to design software control structures which can eliminate or sufficiently constrain a computer from sending unsafe control signals using logical constraints rather than physical constraints? The author offers six explanations. First, computers can have infinitely expanding state spaces comprised of an infinite number of hazardous states. Second, programmed computers have shape-shifting protean behavior which gives them unpredictable, non-continuous (thus non-intuitive) emergent behavior. Third, because it’s imaginary, it’s very easy to build software with unmanageable complexity. Fourth, software control signal interfaces are invisible and physically unconstrainable. Fifth, software design specifications are arbitrary and semantically ambiguous, and the software engineering culture of information hiding can also hide critical security information. Lastly, untrustworthy software administrators deliberately design systems which give themselves abstract power and control authority.
There is another reason why software’s lack of physical constraints contributes to systemic security problems – one that surprisingly few scientific papers have mentioned. Software gives administrators lots of abstract power and control authority over other people’s computers, and there’s often no way for users to physically constrain software administrators from systemically exploiting or abusing their special permissions or control authority. In other words, software represents a new form of abstract power hierarchy, where someone with extraordinary asymmetric amounts of abstract power must be trusted not to exploit it.
- asymmetric amounts of abstract power - the same problem as with governments around the world
Without being able to physically constrain software commands, software must necessarily create trust-based systems where users are inherently vulnerable to systemic exploitation and abuse of untrustworthy or unethical computer programmers who award themselves abstract power and control authority over the system. … Regardless of whether a rank-based resource control structure is formally codified using rules of law or software, whenever special permissions are granted to specific ranks within an abstract power hierarchy, the same systemic security problems re-emerge. … No matter how well software’s control structures are designed, software alone has no capacity to physically constrain the execution of unsafe control signals – the only way this can be done is to physically constrain the underlying computer.
Herein lies one of the most significant but unspoken security flaws of modern software: it creates a new type of oppressive empire. A technocratic ruling class of computer programmers can gain control authority over billions of people’s computers, giving them the capacity to exploit populations at unprecedented scale. These digital-age “god-kings” are exploiting people’s belief systems through software, data mining people and running constant experiments on entire populations to learn how to network target them to influence their decisions and steer their behavior.
“Yeah so if you ever need info about anyone at Harvard… just ask… I have over 4,000 emails, pictures, addresses, SNS… people just submitted it… I don’t know why… They ‘trust me’ … Dumb f***s.” Mark Zuckerberg

It is still too early to know what long-term impacts computers will have on human metacognition, but one thing is already clear: sapiens have discovered a virtual frontier which blurs the lines between abstract and objective realities even further than it was already blurred by tens of thousands of years of storytelling, in completely new ways that our species has never experienced before. As more people integrate symbol-generating virtual reality machines into their lives, they increase their potential to lose sight of the difference between objective reality and abstract reality – the difference between real versus imaginary things. More and more, people are entrapping themselves in semi-somnambulant dream states where they allow strangers to control what they see, hear, and believe, feeding them with programmed illusions of freedom, serendipity, and choice.
The future envisioned by the Wachowskis in the movie The Matrix appears to be coming to fruition. Modern agrarian sapiens are becoming so engrossed in the shared hallucination of cyberspace that they appear to be losing their grip on objective reality. “The Matrix” has been rebranded as “The Metaverse,” but the dynamics of entrapment and exploitation are still the same,regardless of the semantics. A growing number of people appear to be genuinely confused about the difference between the real world and the imaginary world. In this confusion, they are not grasping the difference between real and imaginary things, most notably the difference between real power and imaginary power. Combining this confusion with a general ignorance of power dynamics in agrarian society, people appear to have no concept of the tradeoff between physical power-based resource control and abstract power-based resource control. This creates an unprecedented window of opportunity for systemic predators. As young, unsuspecting, self-domesticated, and computationally illiterate people continue to migrate into the metaverse, they have no idea how vulnerable they are.
People have tried valiantly to design abstract power hierarchies which keep their populations secure from exploitation and abuse using nothing more than logic, but 5,000 years of written testimony prove that no combination of written logic has successfully prevented an abstract power hierarchy from becoming dysfunctional, exploited, vulnerable to foreign attack, or vulnerable to internal corruption. Physical power has always been needed to correct for these security vulnerabilities.
- Perhaps we as Hiveans also need to apply physical power to destroy certain downvoting predators in this community.
We know that as populations became more inclined to impose severe, physically prohibitive costs on abusive abstract power hierarchies, resource management systems became gradually less exploitative over time. In other words, abstract power hierarchies become less exploitative when people stand up and fight for their rights. Over thousands of years of warfare, the extraordinarily high levels of abstract power and resource control authority wielded by god-kings were eventually reduced to kings, then to presidents and prime ministers. The centralized control of empires and monarchies were eventually decentralized into democracies with carefully encoded checks and balances to restrict people’s abstract power as much as possible. Theologies, philosophies, and ideologies increasingly favored equality and individual rights,
and the rulesets reflected it. This cultural evolution was gradual and filled with regression, but the trend is clear: sapiens will find ways to utilize physical power to dismantle, decentralize, and constrain abstract power hierarchies. Why? Because abstract power hierarchies are demonstrably and incontrovertibly untrustworthy, inegalitarian, and dysfunctional. War is the trend. War has always been the trend. If there’s one thing that agrarian society has made explicitly clear, it’s that they’re willing to fight wars to decentralize and physically constrain the abstract power of their own rulers or their neighbor’s rulers. And right now, cyberspace is missing a cyber warfighting protocol for digital age society to physically protect and defend their digital rights.
- "abstract power hierarchies are demonstrably and incontrovertibly untrustworthy, inegalitarian, and dysfunctional" - just as hivewatchers and his cronies. And, yes, we will also win the war against these illiterate schmocks and will decentralize that power.
Using physical constraints to improve cyber security is not a new concept. For example, a common cyber security strategy in many organizations is to physically remove hardware (e.g. USB drives) in the computers to physically prevent belligerent actors from stealing sensitive data from a given computer network or uploading malware to it. US military personnel physically secure their encryption keys by carrying them on specially-designed common access cards (CACs) in their wallets. The same principle also applies to strategies like air-gapped networks. An air gap represents a real-world physical constraint applied to the underlying state mechanisms of a given computer network.
It is theoretically possible to create computer programs that are inherently secure because it’s either physically impossible or too physically difficult to put them into a hazardous state, simply by intentionally applying physical constraints to the underlying state mechanisms running the software. It is also theoretically possible to design computer protocols which can apply real-world physical constraints to other people’s computer programs in, from, and through cyberspace. The protocol is called proof-of-work.
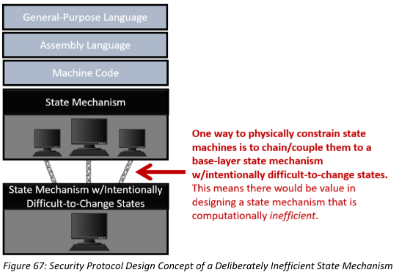
The author challenges the reader to think of an open-source protocol as infamous for its computational inefficiency as Bitcoin. Bitcoin is constantly criticized for how much power is consumed by the computers which run it. What is not understood is why computational inefficiency is an incredibly useful cyber security feature, not a bug. In other words, Bitcoin’s computational inefficiency is its primary value-delivered function – it’s the thing that has been missing in cyber security that is needed to physically constrain belligerent actors, rather than (continue to fail to) logically constrain them.
Proof-of-Work Protocols are Literally Proof-of-Power Protocols
It is imperative for the reader not to overlook the fact that proof-of-work protocols very specifically create real-world physical costs that can be measured in watts. These protocols are computationally inefficient not just because of how many calculations they require, but because of how many watts must be consumed to make those calculations. By using a deliberately inefficient protocol like this, a person or
program applies a real-world physical cost on the execution of control signals sent by other people or programs operating on different computers. To emphasize this point, the author will interchangeably use the term “physical cost function” instead of “pricing function” and “proof of power” or “bitpower” instead of “proof-of-work” where the term “physical cost” refers to the real-world physical deficit of electric power (a.k.a. watts) required to generate a proof of power.
As previously discussed, the first proposed use case for cost function protocols was to serve as a countermeasure against DoS attacks – specifically email spam. This was something that multiple computer engineers recognized as a simple and attractive use case. Adam Back originally called proofs-of-work “stamps” rather than proofs. The name “stamp” was chosen because the original use case of his protocol was to improve email services. The term “stamp” also highlighted how the proofs generated by his software aren’t sequentially reusable, just like real mailing stamps aren’t. The term “proof of work” didn’t appear until two years after Back introduced his prototype. Only after “proof of work” became organically popular terminology did Back call his design concept a proof-of-work protocol. … It didn’t take long for people to start exploring how to use physical cost functions for other use cases beyond securing email browsers against spam. Some software engineers started exploring how to create physical cost function protocols to create sequentially reusable and transferable proof-of-power receipts. When this happened, people abandoned the word “stamp” and started using the names of other abstract objects like “token” or “coin.” … proof-of-work was universally described as a cyber security protocol for fifteen years of peer-reviewed academic literature prior to the release of Bitcoin. In other words, proof-of-work protocols have been known as cyber security protocols for twice as long as they have been known as monetary protocols.
Instead of physically constraining attackers via forces displacing masses like normal barriers do, electro-cyber domes physically constrain attackers via electric charges passing across resistors. But as Einstein famously observed, matter is swappable with energy, so kinetic physical constraints can theoretically be swappable with electric physical constraints for certain applications. Physical power is physical power regardless of whether watts are generated kinetically or electrically. Thus, the physics behind electro-cyber dome security systems is similar to any other physical barrier even though it doesn’t look anything like a traditional physical barrier. Just like any other physical barrier, electro-cyber domes secure people
against attackers by increasing the number of watts attackers must expend to succeed. Security is achieved the same way it’s always achieved using any other kind of physical barrier. At a certain threshold, attackers simply don’t have enough physical power to succeed. The armor is too strong, the moat is too wide, the wall is too tall, or in this case, the amount of electric power needed to send belligerent control signals is simply too high.
The core concepts of this overarching theory are grounded to more technically detailed theories discussed in this section. Some of these ideas were inspired from data collection, but others are completely original. The most important takeaway from this technical discussion is that Bitcoin (the system) may not be special because it represents a new type of software, but because it represents a new type of computer. The author believes that Bitcoin represents the invention of what he calls a “planetary state mechanism.”
It’s theoretically possible that Bitcoin could be emerging as the base-layer operating system for a planetary-scale computer. This would mean that Bitcoin (the system) doesn’t just represent a new type of software protocol, it represents a new type of computer – a new type of computer called a planetary-scale computer. If this theory is valid, then global adoption of Bitcoin simultaneously represents the global-adoption of a planetary-scale computer – the exact thing which speculative philosophers like the Berggruen Institute’s Antikythera program theorize would have drastic geopolitical implications. … Not only would it be possible to utilize the planet itself as a large, heavy, slow, and energy-intensive computer, the infrastructure and circuitry required to accomplish this has already been built – we call it the global electronic power grid. Herein lies a simple, but profound idea: to create the world’s largest, heaviest, most energy-intensive, and most physically-difficult-to-operate computer ever built, we could simply utilize our planet’s energy resources as the controllable physical-state-changing mechanism of a planetary-scale computer, where the globally-distributed electronic power grid serves as its circuit board. This design concept is [here: ]
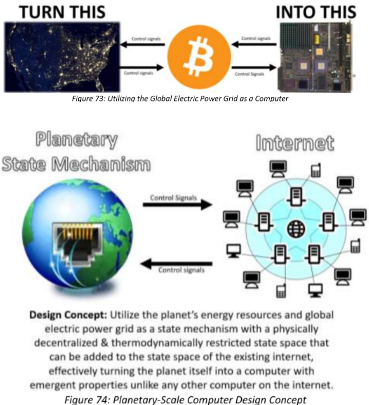
But what could possibly be the benefit of turning the electronic circuitry outside of our internet into a programmable computer in and of itself and then plugging it back into the internet? The benefit is that it would create a physically decentralized and thermodynamically restricted section of the internet over which agrarian society would be able to compete for control authority in a zero-trust, permissionless, and egalitarian way using a physical power competition. As a complex emergent benefit of that physical power competition, the global population would be able to gain and maintain decentralized control authority over that part of the internet.
With the invention of this type of planetary-scale computer, agrarian society would be able to use their own energy resources to battle for control authority over this planetary-scale computer the same way all organisms in nature (including and especially modern agrarian sapiens) have always used physical power competitions to battle for control authority over resources. And as a complex emergent benefit of this ongoing electric power competition, agrarian society would be able to gain and maintain decentralized control authority over this new digital-age resource. As established in section 4.9, one of the primary value-delivered functions of physical power competitions (a.k.a. warfare) is physical decentralization of control over Earth’s natural resources. There’s no reason to believe this wouldn’t also apply to power competitions for control over the natural resources comprising a planetary-scale computer. … In short, it’s possible to think of several reasons why people would benefit from a physically decentralized and thermodynamically restricted state space of the internet created by a planetary-scale state changing mechanism which converts our electric power grid into the motherboard of a planetary-scale computer. … If people were to build a planetary-scale computer like the one described here and plug it into the internet, this could not only usher in new approaches to cyber security, but it could also dramatically change our approach to digital-age national strategic security, particularly how it relates to securing digital information and enforcing digital contracts.
A Planetary-Scale Computer could Dramatically Improve Society’s Global Electric Power Grid
There’s another major benefit of utilizing a planetary-scale state mechanism as a large, heavy, slow, and energy-intensive computer. If society were to create a planetary-scale computer which utilized global energy resources as its state-changing mechanism (akin to transistors), as well as the global electric power grid as its circuitry (akin to a motherboard), then society could theoretically unlock the benefits of Moore’s law for our energy infrastructure. Engineers love making their systems more efficient, particularly their computer systems. As previously mentioned, computer engineers are obsessed with optimizing their computer systems to make them faster, cheaper and more energy efficient. This phenomenon is so predictable that we colloquially refer to it as Moore’s law.
If society created a planetary-scale computer, then populations would naturally seek to improve the speed and efficiency of this computer’s circuitry. Societies might search for cheaper and more abundant sources of energy with more optimized infrastructure designs so they could make their portion of the planetary-scale computer faster and more inefficient. There would also be an incentive to do this to gain a competitive edge in the form of more control authority over the planetary computer as a whole. These dynamics would create a counterintuitively beneficial feedback loop for society. The wide-scale adoption of a deliberately large, heavy, slow, and energy-intensive planetary-scale state mechanism would motivate society to try to continuously improve it by creating faster, more efficient, and more optimized electric power infrastructure. In other words, the complex emergent benefit of turning the global electric power grid into the circuit board of a planetary-scale computer would be to unlock Moore’s law for the global electric power grid. By simply turning the power grid into a computer chip, society would be able to utilize its insatiable drive for faster and more efficient computer chips to create a faster, more responsive, and more efficient power grids.
| In my opinion, this is one of the most important advantages of Bitcoin: it incentivizes the production of usable energy. Let's hope it will accelerate the addition of new energy sources (such as fusion) and lead to energy abundance. | Meiner Meinung nach ist dies einer der wichtigsten Vorteile von Bitcoin: Er schafft Anreize für die Produktion von nutzbarer Energie. Hoffen wir, dass dies die Hinzufügung neuer Energiequellen (wie z.B. die Fusion) beschleunigen und zu Energieüberfluss führen wird. | En mi opinión, ésta es una de las ventajas más importantes de Bitcoin: incentiva la producción de energía utilizable. Esperemos que acelere la incorporación de nuevas fuentes de energía (como la fusión) y conduzca a la abundancia energética. |
People mistakenly believe that Bitcoin’s substantial energy usage is a bug, but it’s actually its primary value-delivered feature. The physical state changes of the surrounding environment produced by physical cost functions manifest themselves as deficits or vacuums of electric power which must be filled by electric power producers connected to the global electric power grid. This quantity of electric power represents a continuous-time signal that can be transferred, received, modulated, digitally sampled, and stored as digital information just like any other power-modulated electromagnetic signal. The primary differences are simply power intensity and production cost.
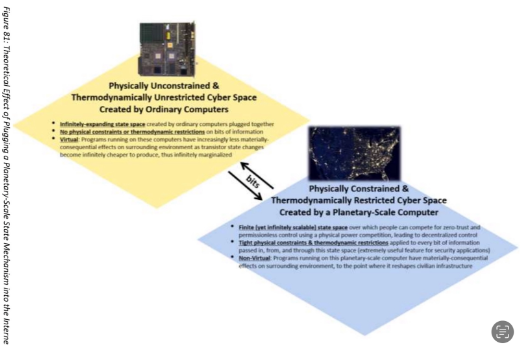
In the future, proof-of-work, a.k.a. proof-of-power, a.k.a. proof-of-real, a.k.a. physical cost function protocols like Bitcoin could serve as the dominate mechanism used by digital-age societies to map or anchor elements of the legacy version of the internet to the new version internet, thereby serving as the world’s globally-adopted “proof-of-real” protocol. Regardless of whatever arbitrary name people give to protocols like Bitcoin in the future, the point is that Bitcoin could become instrumentally more important than merely a financial system. Bitcoin has the potential to become integral to the development of a completely new internet infrastructure and a completely new type of cyberspace. It is possible that what we are seeing with the global adoption of Bitcoin represents a “strangler pattern” playing out for the existing internet architecture – we could be modernizing a large, monolithic computing system right now by gradually replacing services performed on the legacy system with services performed on the modernized system, and it could just be that financial information exchange simply represents the first of many microservices to be performed on a modernized architecture of the world-wide web.
It is Physically Impossible for Proof-of-Stake Protocols to Replicate Proof-of-Work Protocols

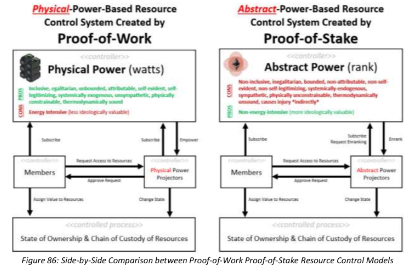

Summarizing the core theoretical concepts about bitpower presented so far: bitpower protocols like Bitcoin look inefficient to those who might not understand the complexities of computer theory, cyber security, agrarian power dynamics, human metacognition, or the basics of how living organisms establish dominance hierarchies to manage control over their resources. Consequently, people don’t understand how and why people would be inclined to summon large quantities of electric power from the environment, convert it into machine-readable bits of information, and use it for systemic security purposes – particularly to countervail the threat of people wielding too much abstract power via the computers they program.
What makes Bitcoin’s design remarkable is not merely that it solved the so-called double spend problem or the so-called Byzantine general’s problem. What makes Bitcoin remarkable is that it appears to have created a non-lethal equivalent to warfighting that achieves the same complex emergent benefits of traditional warfare using the exact same social protocol of engaging in a physical power competition, but it removes the mass, thus eliminates the capacity for human injury. The problem Nakamoto faced with determining how to establish zero-trust and egalitarian control authority over bitpower is therefore not merely a challenge faced in distributed computing; this is a challenge that sapiens have encountered since at least the dawn of the Neolithic age. Sapiens have been struggling to figure out a zero-trust and permissionless way to manage valuable resources and establish pecking order without injuring each other, and they have never succeeded to date. The most they have been able to achieve is creating temporary and fleeting reprieves from the destruction and injury of warfare; they have never been able to remove the destruction and injury of warfare altogether. If Nakamoto successfully solved the challenge to which he’s often given credit, that could not just mean he solved a core challenge in computer science, that could mean he solved a core challenge for agrarian civilization: he created a non-lethal form of warfighting. In other words, he created softwar.
From a systemic perspective, Bitcoin functions similarly to how a militia functions. A large group of people project lots of physical power to preserve freedom of action within a particular domain, giving nations the ability to exchange goods (in this case bits) with another nations without interference. The form of the militia is different because the form of the domain is different. Cyberspace is disembodied and transnational, so it makes sense that a cyber militia would be disembodied and transnational too.
… No matter how competitive an electro-cyber power competition gets, it seems unlikely that it could lead to a state of mutually assured destruction because there’s nothing inherently destructive about developing increasingly efficient forms of electric power projection technology. In fact, society could potentially benefit from this power competition. It would motivate society to search for increasingly more clever technologies to generate more power more efficiently, as well as develop faster and more efficient hashing computers.
| This was a long book (far too long) due to a lot of repetitive sections. Instead of 365 pages it should have 150. But I find its content very good and gained some important insights. We will see if Jason's claims will play out in the years to come. With Bitcoin's ETF approval we may have made a big step in that direction. | Das Buch war lang (viel zu lang), da sich viele Abschnitte wiederholten. Anstelle von 365 Seiten sollten es 150 sein. Aber ich finde den Inhalt sehr gut und habe einige wichtige Einsichten gewonnen. Wir werden sehen, ob sich Jasons Behauptungen in den kommenden Jahren bewahrheiten werden. Mit der Zulassung des Bitcoin-ETF haben wir vielleicht einen großen Schritt in diese Richtung gemacht. | Este es un libro largo (demasiado largo) debido a muchas secciones repetitivas. En lugar de 365 páginas debería tener 150. Pero su contenido me parece muy bueno y he adquirido algunas ideas importantes. Veremos si las afirmaciones de Jason se cumplen en los próximos años. Con la aprobación del ETF de Bitcoin puede que hayamos dado un gran paso en esa dirección. |
| I hope you enjoyed these excerpts and don't consider them plagiarism. | Ich hoffe, Euch haben diese Auszüge gefallen und dass Ihr sie nicht als Plagiat betrachtet. | Espero que haya disfrutado de estos extractos y no los considere plagios. |
Ceterum censeo hivewatcherem esse delendam. (Furthermore, I consider that hivewatchers must be destroyed.)
Have a great day,
zuerich




!LOL
Posted using MemeHive
lolztoken.com
Because it was mugged.
Credit: reddit
@zuerich, I sent you an $LOLZ on behalf of holovision
(3/10)
ENTER @WIN.HIVE'S DAILY DRAW AND WIN HIVE!
This is really an interesting story worth reading
I love how he explains computer software, which are hypostatized concepts, they want us to pretend that they are real. Although society has adopted the habit of describing software as if it were composed of object orientation, it is not. It is simply an abstraction technique used to facilitate understanding of the complex.
When a program is "removed" from a computer, nothing is physically removed from the machine.A herein lies the fundamental challenge of software security engineering; it requires an engineer.
The only physical change that occurs is a change of state in the machine's circuitry. A switch is flipped or electrons move from one side of a floating gate transistor to the other.
From the exposition in this Post. I have been able to realize. Of what Computer Science programs are. Have a nice evening.
Thanks for your comment, @rammargarita!
Yes, this explanation (though plausible) was also new for me. Humans try to make abstract concepts as concrete as possible.